Have you ever encountered content that was “not available in your region” while surfing the web?
Have you ever wanted to watch one of the shows that Netflix has available in another country?
I bet you have, especially if you live outside the United States of America. The solution to this issue is easy enough: you can use a proxy server or VPN service. But there are two issues with that approach:
- All your internet traffic is going through the VPN. If this can result in very notable delays when surfing your normal websites.
- You usually have no insight into what kind of logging you VPN provider does. So you really shouldn’t do any sensitive stuff over that connection.
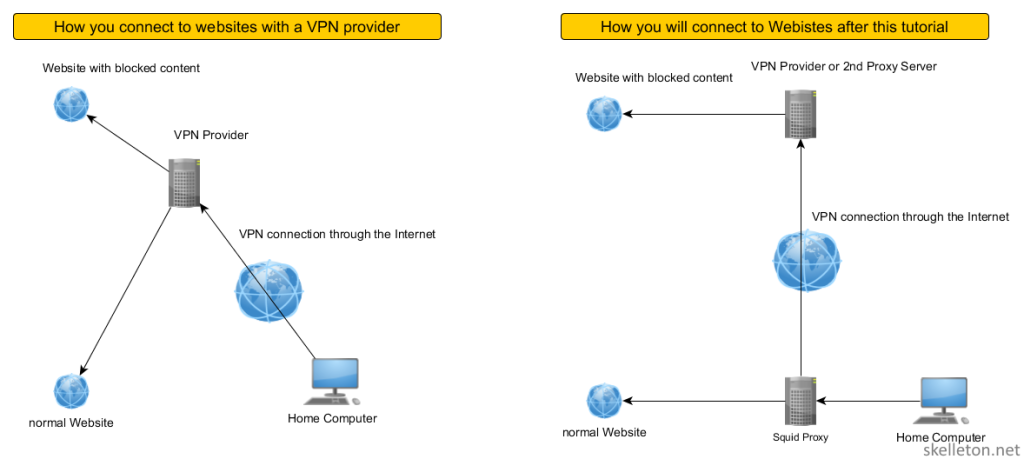
Ideally you would want all of your normal surfing to go out through your normal internet connection and all the region specific stuff through a VPN or some other proxy.
And you can actually build something to do this with Squid. Squid is an Open Source proxy server.
A proxy Server sits between your browser and the websites you want to surf to. It accepts all your requests to surf to certain websites and processes them according to its configuration. Once it has determined that the request is valid, it will contact the web server for you and fetch the content you want. It will then forward it to your browser.
Since it sits in the middle of your traffic, it is the perfect place to redirect some traffic through another connection.
This diagram visualizes the difference between the two options for you:
And this is really just the start of your capabilities of Squid. While this tutorial will only show you a few basics of squid and how you can redirect some content over a VPN or another Squid server, there is so much more that can be done with Squid:
- Are you on a connection with a fairly low Volume available (like some mobile contracts)?
No problem! Just crank up the caching in squid and repeated visits of the same website won’t be as demanding on your volume. - Have kids that that visit bad websites?
No problem! You can use squid to filter the internet by pretty much any criteria your want. And you can do it on a per user or computer basis if you need to. - You hate ads on websites, but maintaining you Ad-Blockers across all devices is annoying?
No worries! You can use squid as your Ad-Filter.
Continue reading How to escape geoblocking by content providers with Squid