The Problem
A while ago somebody came to me with a problem. A bunch of Services on their Server stopped working. The admin password in the documentation didn’t work. The Server in question was a SBS with a bunch of additional software that was critical to the business. My questions for Backups were answered with silence.
Click here to skip all my gabbing and warnings. And go directly to the guide.
The Options
Obviously backing up all the data With a Boot CD and reinstalling the Server was to be avoided at all costs, but that Option is on the table if there are actually any recent backups (check them before trying to restore them to the server). I had reset Local Windows user accounts with before without much of a problem. But domain accounts are a very different issue and the tools for resetting local accounts don’t work for them. It did not help that Microsoft’s official stance on this problem is something along the lines of: if you loose the password to your only domain admin it can’t be recovered or reset.
Well that is not entirely true since you could restore a Backup of the Active Directory from a point time when your documented password still worked. Though this could cause a whole bunch of other issues. And in this scenario it is likely, that you will be told that it worked yesterday. Of course this will turn out to be wrong.
After a little bit of research (search Google for the problem and ignore Microsoft websites) I found a fast, easy and almost painless solution. The only issue with solution is, you will need to reboot the server from a Boot CD.
A few words of warning
I tested this with a Windows Small Business Server 2008. While this guide should also work for other Windows 2008, 2008R2 and even Windows 2012 based Domain Controllers, I have not had to test it yet and I can’t guarantee that this will work on those Operating Systems.. I am especially not sure if Windows Server 2012 still executes the ease of use utility with system rights and if the executable file is still named the same.
You should also know, that there is no guarantee that Microsoft won’t fix this in the future, since this is a security loophole that could be used to gain unauthorized access to the network.
The Solution
I am providing this step by step guide for fellow tech support people, who might be confronted by such a situation by no fault of their own. If you bring all the needed Tools and the Server boots decently fast, you will be done within a few minutes. And you should be aware, that doing this is illegal in many countries if you are not authorised by the owner of the server. So get the job in writing with a signature from the companies boss before you start.
With that said, just follow these steps to save the day:
- First you need to gain local access to the server (though an IPMI that allows you to boot from an iso file should work as well).
- Now you need to boot from any kind of Boot CD that allows you write access to NTFS File systems. For this you can use one of the many Recovery Linux Distributions out there or even the Windows Install CD that came with the server. In case of the Windows CD you want to open the windows repair console.
I should mention here, that the Operating System you are booting into should support the disk controller that is connected to your windows drive(s) - Now navigate to the system32 Folder within your Windows Folder. In the Windows Recovery Console It might look something like this (though your windows drive does not necessarily have to be C:):
cd C: cd C:\windows\system32
- Once you are there you have to replace the Windows Ease of Access Tool with the Windows command line. Since you will want to reverse this change once you are done, I would advise against any action that would permanently remove this utility. The Ease of Access Utility is the file “utilman.exe” and the command line is “cmd.exe”. With the Windows Recovery Console you would accomplish this with the following commands:
rename utilman.exe utilman.exe.old copy cmd.exe utilman.exe
- After you replaced the utility, you need to reboot into the windows Installation.
- Click The Button shown in the Windows 7 logon screen. While this is not one of the Server Operating Systems, The logon Screen is pretty much the same for them.
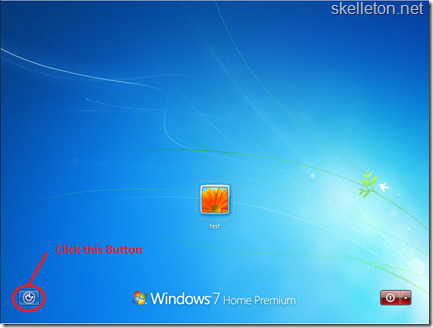
- Clicking this Button will open a cmd window with system privileges. In this window you should type the following (replace Administrator with the username of you Domain Admin):
net user Administrator newpassword123
- You can log in now. You should put to original utilman.exe back in its original place. The easiest and cleanest way to do it is rebooting and doing it with your boot cd again.
Once you are done, you might want to inform the person running the server about the importance of Backups and proper documentation.
No windows\system32\utilman.exe file on my SBS2008 server. Any idea why? Either the file is hidden or in some other location. The utility is still available at logon screen so I know it is somewhere.
The only thing I can think of on the fly is multiple windows Directorys possibly from upgrading or an old install still being present on one of the volumes.
In that case you should check the other volumes.
If you are using a linux boot disk to find the file, try searching for Utilman.exe(with an upper case U). Linux is case sensitive when looking at file and folder names.